
Identity security without the complexity.
Centralize visibility, enforce Zero Trust policies, and eliminate manual access reviews across hybrid infrastructure from a single platform.


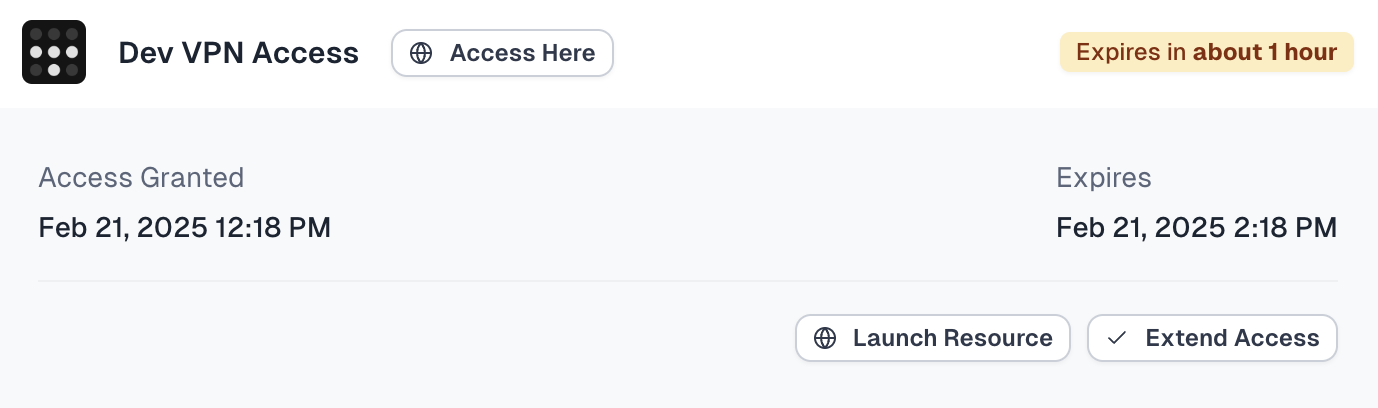















Identity used to be so simple...
Identity security is no longer managing usernames & passwords to resources in your network. Now, your security team struggles to manage the risks of employees with multiple identities accessing countless apps, systems and resources.
95%
80%
90%
34%
Finally, a unified platform to visualize your identities and control access
Ploy unites identity silos by integrating with your existing IAM solutions, critical infrastructure and SaaS. Giving you, for the first time, a comprehensive and unified view of all your identities and access paths. From here you're able to automate the identity lifecycle, empower employees with JIT temporary access, automate access reviews and identify anomalous access.



Untangle your access paths
Instantly visualize your identity access paths to critical and sensitive resources, all unified in Ploy.
Finally manage the identity lifecycle
HRIS integrations enable Ploy workflows to run days or weeks before an employee joins, so you're not caught out with last minute onboarding.





Seamless least privilege JIT access
Empower your employees to request only what they need, when they need it.
Automate user access reviews
90% less time and effort spent on user access reviews. Ensure compliance, reduce standing privileges, and enhance overall security.





Stay compliant at scale
Ploy streamlines evidence collection, access certifications and auditor reporting so you can be ready for any audit.
"Ploy has enabled us to completely automate employee onboarding and offboarding, saving us 150 manual actions, clicks, and hours of time per employee"
Senior IT Services Manager at Liberis

Explore use cases
Automate access reviews
90% less time and effort spent on user access reviews. Ensure compliance, reduce standing privileges, and enhance overall security.
Learn moreSelf-service access
Enable employees to self-serve the apps and roles they need with the app directory. Less IT headache. Less waiting. More productivity.
Identity lifecycle
Simplify the employee lifecycle: automatically create user profiles, manage resource access and permissions without lifting a finger.
Next-Gen IGA
Gain full visibility across complex cloud environments, collect audit evidence and enforce access control policies.
